Discover how EBIOS Risk Manager can be used in a concrete case, with the risk analysis of a medical imaging center. Workshop by workshop, results are presented to understand the expectations at each step.
A risk analysis method
The risk analysis with EBIOS Risk Manager method allows to establish an iterative and sustainable risk management strategy. This method provides a complete vision of the risks for IT security managers whatever the field of application.
To help in the realization of these analyses, ALL4TEC develops and deploys the Agile Risk Manager tool, labeled by the ANSSI. It allows to easily conduct relevant risk analyses based on the EBIOS Risk Manager method.
Indeed, based on graphical representations, Agile Risk Manager presents the different results of the workshops to be conducted during the analysis.
Why a radiology medical center?
The health sector is a critical area, as it is closely linked to human safety. This is particularly true for radiology services, which, due to their interdisciplinary and nodal nature, constitute a central element in the health sector. Their protection is therefore a major imperative.
Moreover, these services are totally dependent on Information and Communication Technologies (ICT) as they rely on multiple devices and systems. They include in particular:
They include in particular:
- Medical equipment (MRIs, Scanners, etc.) required for patient data acquisition
- Data processing, reproduction and storage systems
- Interconnection and communication interfaces
Finally, recent cyber attacks, particularly those of the “Ransomware” or “DDoS” type, are increasingly targeting medical treatment entities. In this regard, we will mention “Wannacry” which targeted certain hospitals in Great Britain, but also the attacks perpetrated against the University Hospital of Rouen as well as the Public Assistance Hospitals of Paris (AP-HP).
Protecting material and informational radiological assets is therefore crucial. It is absolutely necessary to anticipate and adopt a preventive approach, through a risk analysis.
The EBIOS Risk Manager method is based on an iterative and agile approach, built around workshops. Each workshop chooses a particular point of view and a specific issue.
The passage through all these workshops will lead to build, step by step, a relevant and complete risk analysis, focused on the most significant risks.
Workshop 1 - Scope & security baseline
Workshop 1 helps to define the general perimeter of the analysis, identify what we want to protect, what we fear, and what measures have already been implemented. The point of view is that of the defendant, in this case the radiology practice or center.
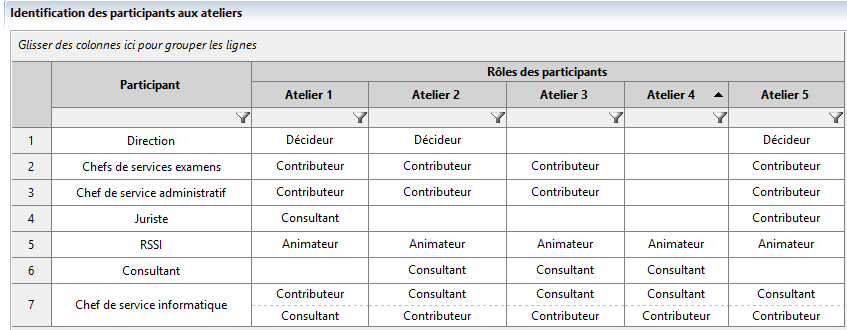
We have opted for a complete risk analysis with strategic and operational cycles of 3 years and 12 months respectively. We have defined the Roles and Responsibilities Matrix (RACI) which allows us to plan the steps of our analysis as well as the people involved in each workshop.
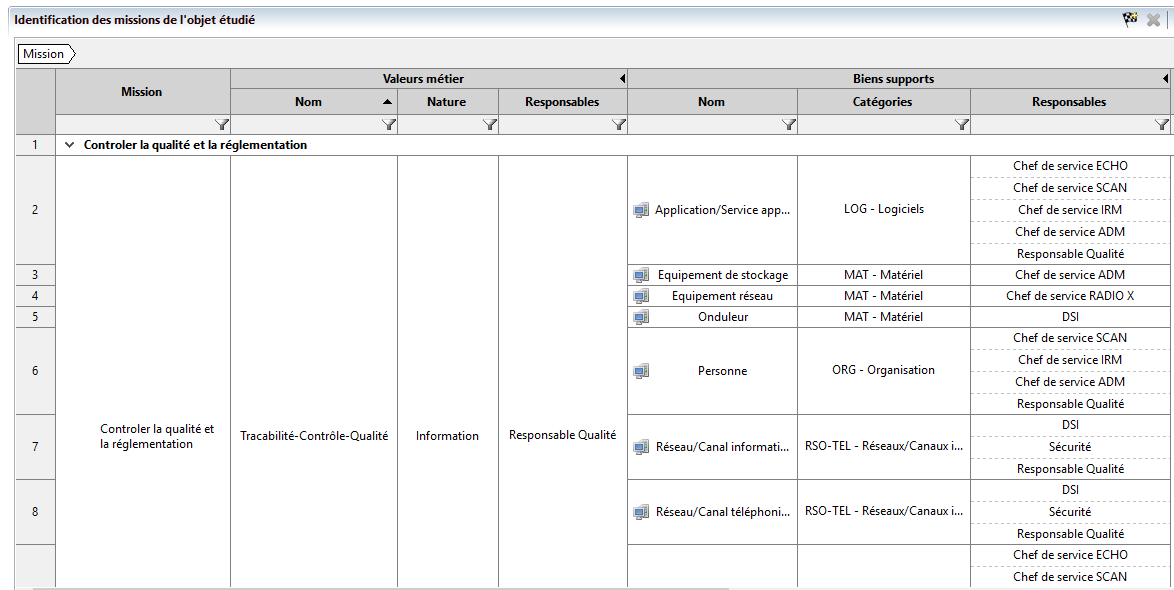
Next, we determined the business values (BV) that represent the business processes and information of the radiology department: MRI, CT, standard radiography, ultrasound, patient administration and management, and quality control.
For each Business Value (BV), as described in the method, we associate the appropriate support assets and managers. Depending on security needs in terms of availability, integrity, confidentiality or traceability, each BV may be confronted with one or more dreaded events (FEs) that it is essential to explain.
For example, the system for transmitting and archiving images between modalities (PACS – not to be confused with the Continuous Security Improvement Plan proposed in Workshop 5) is a critical element for any radiology site.
This is why the “sabotage of the MRI-PACS interface” constitutes in our analysis a critical FE for the “MRI” BV. It is important to classify the FEs in order of severity. This is measured based on their respective impacts (financial, legal, on image, on the safety or health of people, etc.).
During the definition of the security base, in addition to the standards already available in Agile Risk Manager, such as the ANSSI hygiene guide, we introduced two new standards:
- A repository of customized internal measures that defines a set of rules and best practices that can be developed internally for each entity. This will include measures such as video-surveillance or access control, etc…
- A qualitative referential, based on IT security measures standardized in the “LABELIX” Label. This is the official tool for recognizing the quality of services provided by medical imaging practices and services (http://www.labelix.org).
Workshop 2 - Risk sources
Workshop 2 is characterized, unlike Workshop 1, by an attacker-centric approach, referred to in EBIOS Risk Manager as “risk source”.
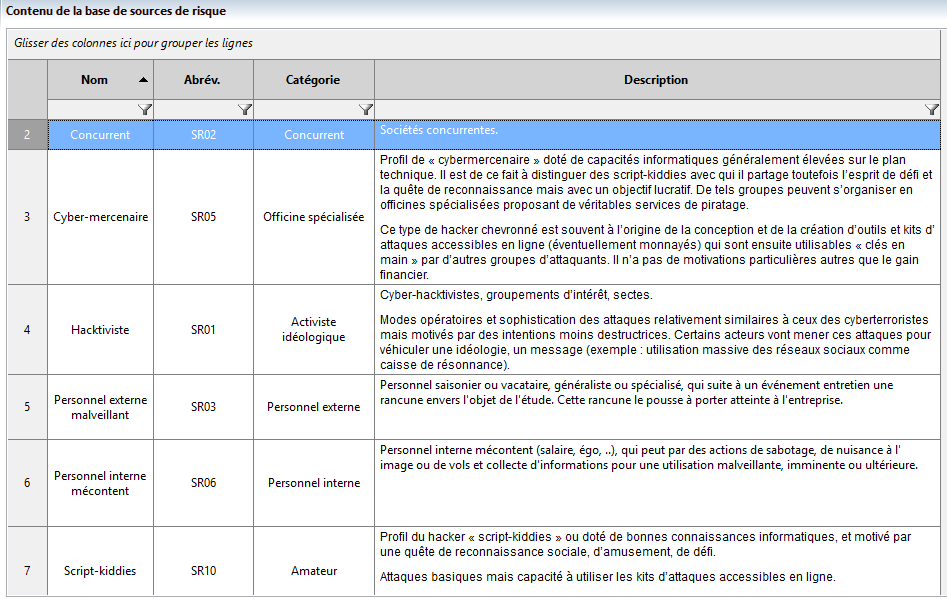
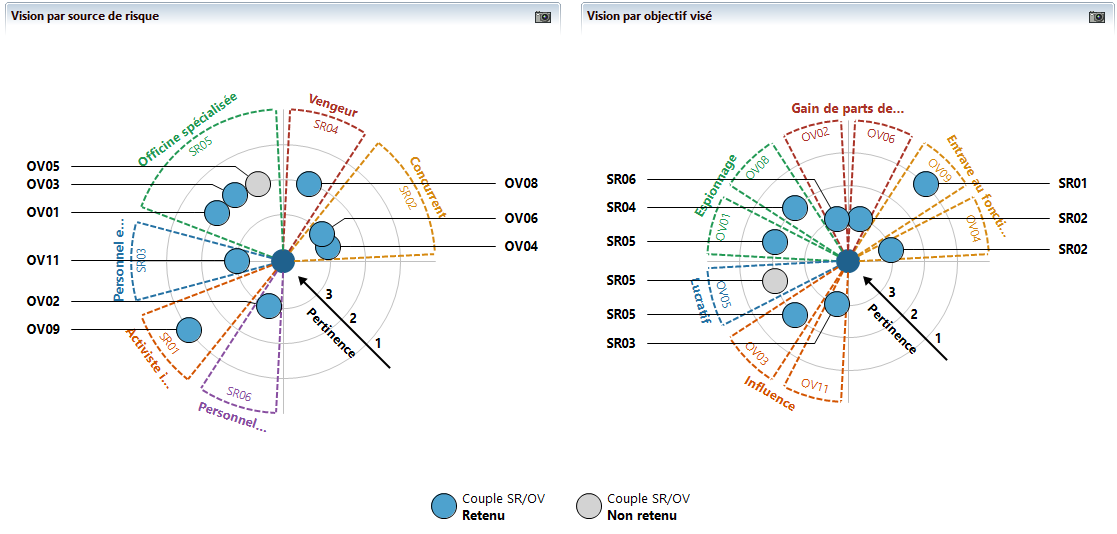
This is why in this workshop, we have first identified the risk sources (RS) that can harm the radiology center: competitor, cyber-mercenaries, malicious external staff, disgruntled internal staff, avenger, etc.
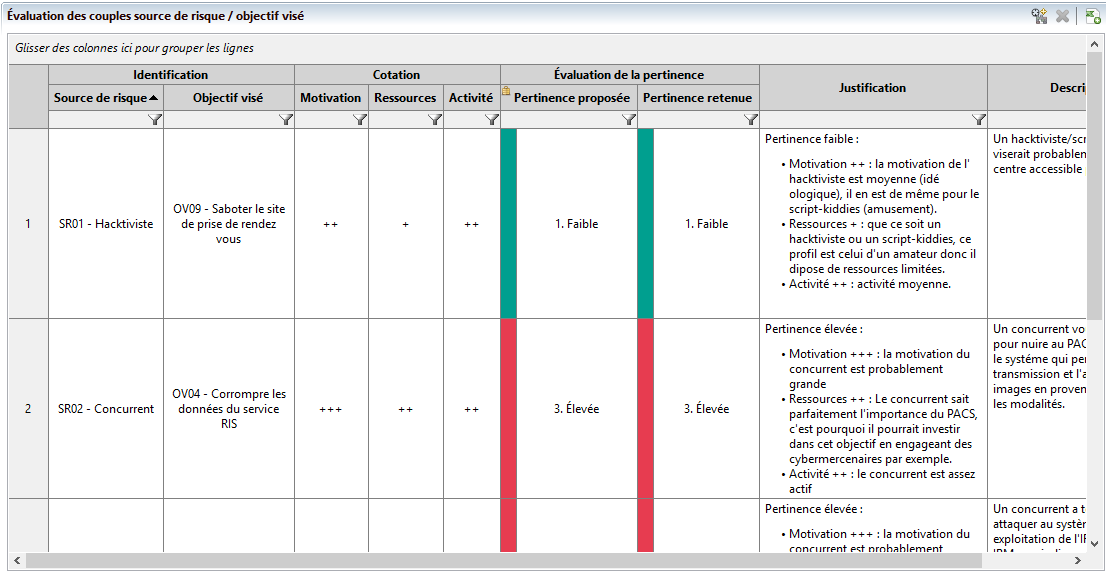
In a second step, each RS is assigned a target objectives (TO) that can be determined from the effects sought by each assailant.
For example, to corrupt the data on the Radiology Information System (RIS) management server, or to corrupt the data of the RIS server, or Cyber mercenary / Sabotage the appointment scheduling site.
Once the RS/TO match is established, it is possible to proceed with its evaluation based on the motivation, resources and activity of the RS. In Agile Risk Manager, this evaluation is carried out graphically and provides a visual representation of the relevance of RS/TO pairs from several angles.
Workshop 3 - Strategic scenarios
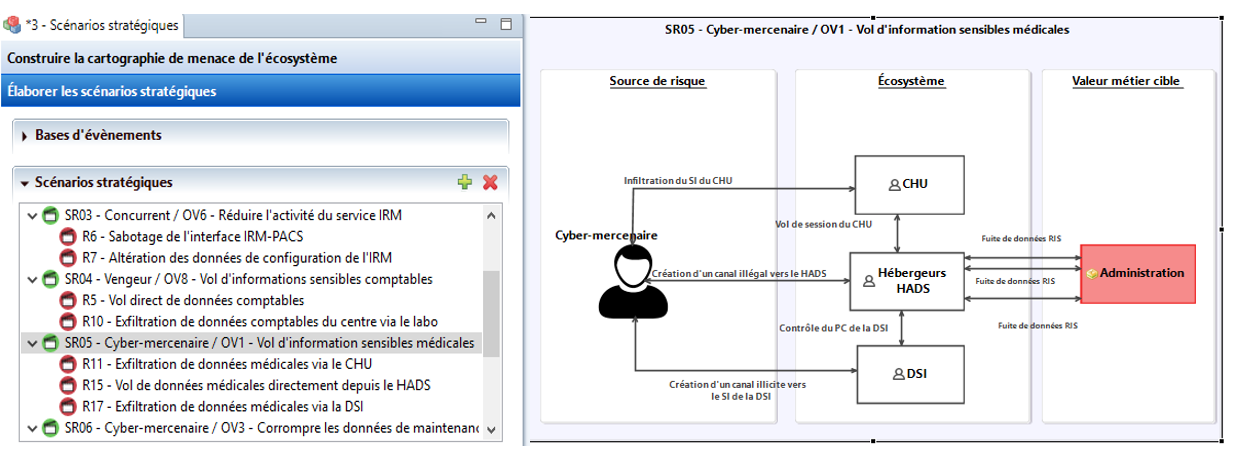
Subsequently, we seek to define the stakeholders who can serve as relays, without wanting to, to the hostile approach of a source of risk.
This is what we call strategic scenarios, associated with the RS/TO pairs. Strategic scenarios are made up of one or more paths of attack. For example, a cyber-mercenary whose objective is to steal medical information from the “Administration – Patient Management” BV (Business Value) could achieve its goal by creating channels for the exfiltration of sensitive data either to the CHU, or to the ISD, which is an internal stakeholder, or directly to the HDSAHP.
The graphical representation allows the different strategic scenarios and their respective attack paths to be visualized.
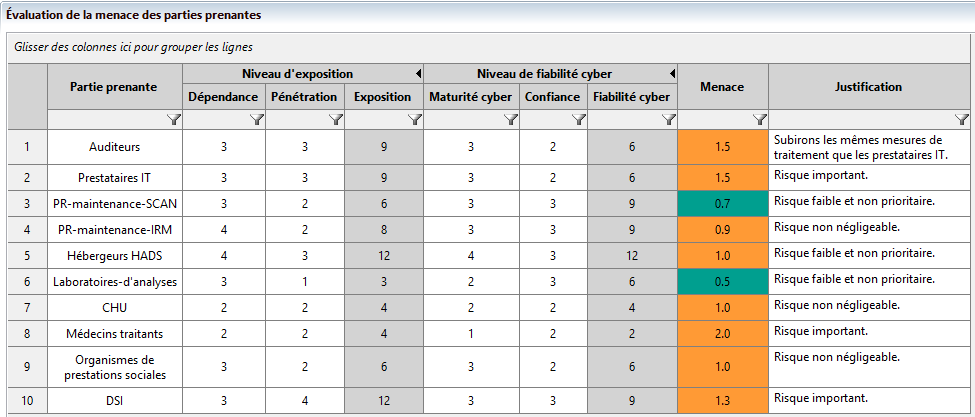
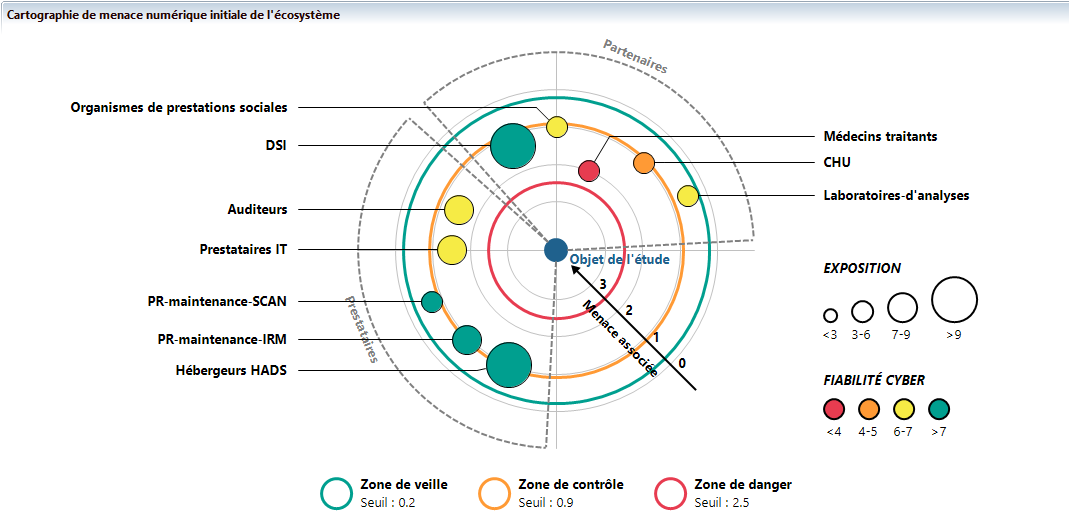
This workshop includes a preliminary treatment of risks according to the EBIOS Risk Manager method. This preliminary treatment leads to the definition of security measures that apply directly or indirectly to the stakeholders and thus allow by their application a reassessment of the stakeholders’ cyber exposure and maturity.
In our example, the application of stakeholder measures has reduced the initial threat level of IT service providers and enabled them to be moved from the control zone to the monitoring zone.
Workshop 4 - Operational scenarios
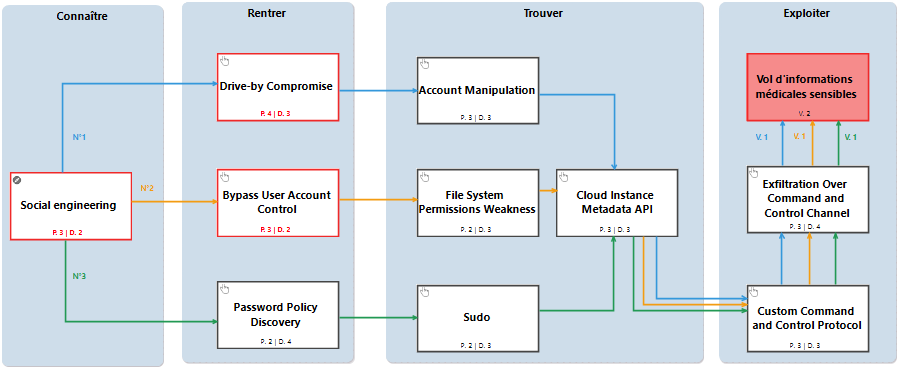
This scenario consists of three different attack paths. We detail below the one concerning an exfiltration by corruption of a public website (blue path on the schema).
- After a reconnaissance, the attacker identifies a website that is regularly accessed by staff with privileged rights at the CHU. Then, the attacker infects the website in question.
- During the visit of the CHU element to the infected site, the attacker corrupts the target’s browser by exploiting a vulnerability and recovers the stored passwords.
- The attacker uses these elements to authenticate on a session from the target to an instance at the HDSAHP where the data from the radiology center is hosted.
- The cyber-mercenary then attempts to access a metadata API instance of the Cloud instance, trying to recover the privileges associated with it.
- Then, the attacker sets up a channel and a custom “command and control” type protocol.
- Finally, the cyber-mercenary fraudulently exfilters medical data from the radiology center, hosted in the HDSAHP Cloud platform.
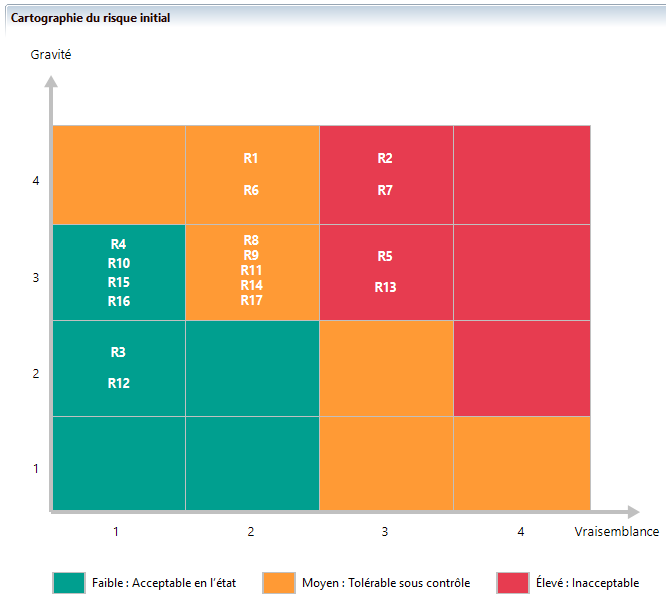
At the end of this workshop, Agile Risk Manager positions all of the analysis risks in the risk matrix based on their severity and likelihood. This is the initial risk mapping.
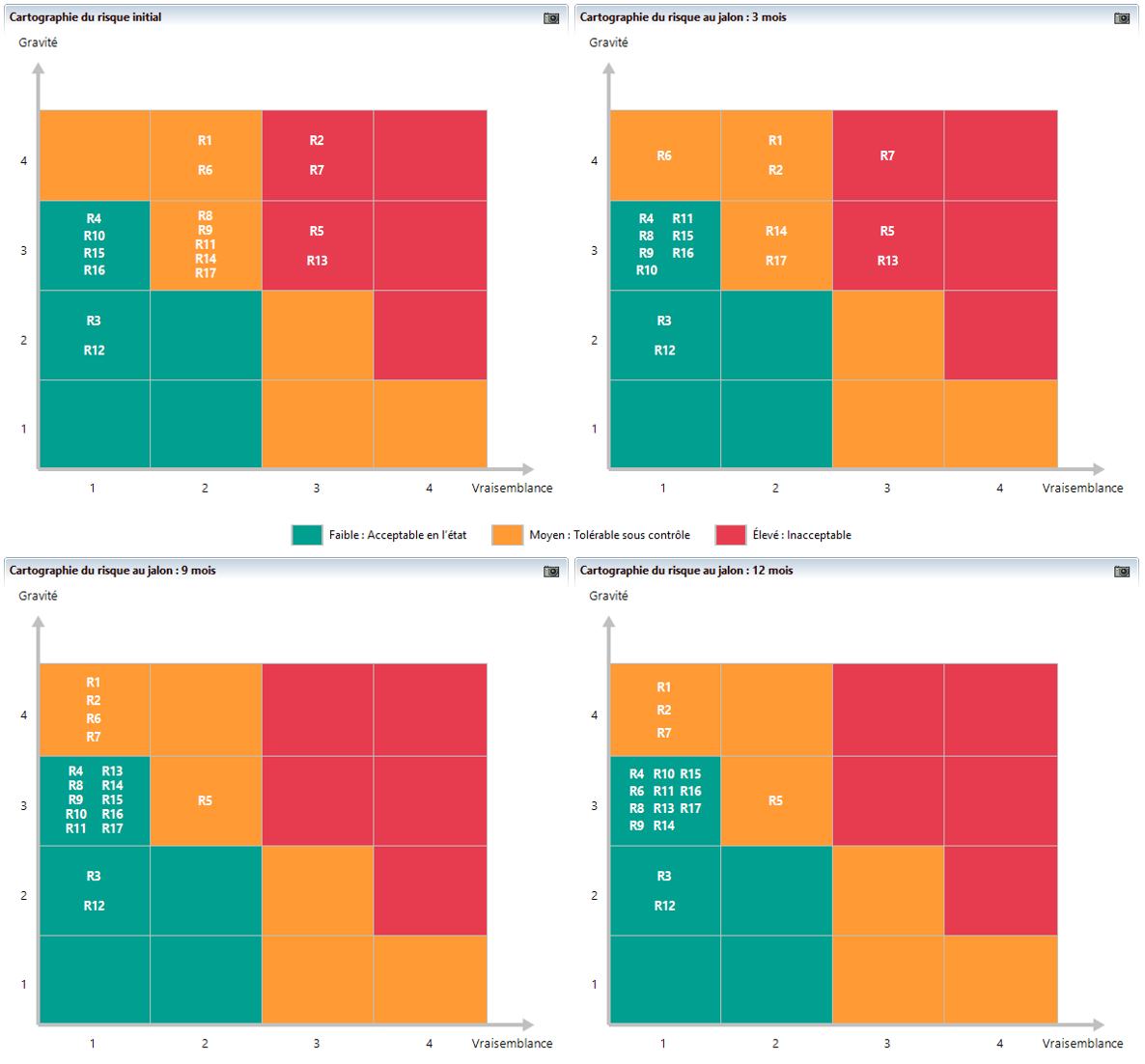
Workshop 5 - Risk treatment
At the end of an analysis cycle, workshop 5 allows the participants to recall all the results obtained previously. bThese results are exploited in a staggered manner over time and give rise to a continuous security improvement plan (CSIP) according to the means and constraints (time, budget, complexity) of the object of the study. The implementation of the CSIP allows a gradual reduction (3 months, 6 months, etc.) of risks, until a satisfactory level is reached that is aligned with the organization’s risk treatment strategy.