The EBIOS Risk Manager method continues its deployment and its adoption is accelerating. In parallel, the Department of Defense specifies a cyber security model which will be adopted internationally. Discover here CMMC in a glance and how EBIOS Risk Manager can help in each maturity step.
The CMMC, what is this ?
A maturity model is a general approach, aimed at improving an organisation’s posture on a particular theme, step by step. The historical and best known model is the CMMI, focusing on IT project management. This principle has since been declined and adapted to other activities and sectors.
The CMMC (Cybersecurity Maturity Model Certification) is particularly interested in cybersecurity. It is based on NIST 800-171 and 800-53. These two standards have until now been the basis on which the subcontracting manufacturers of American institutions, mainly but not exclusively defence, have been working.
These two standards provide precise and relatively complete security measures, but the approach is essentially based on declarations: each structure must assess itself and validate its compliance, or define a remediation plan to achieve it.
The increase in the number of cyber incidents in recent years clearly shows the limits of this type of approach: the DoD (Department of Defense) has therefore decided to switch to a compulsory and binding certification model provided by a trusted third party, to be renewed regularly.
Who is concern by CMMC ?
All subcontractors (direct or indirect) of the DoD are potentially concerned. More formally, those who will have to handle :
- Unclassified controlled data (classified data are covered by other standards)
- Information provided by the DoD in the context of a contract and which is not intended to be disseminated to the public
The only possible exclusion at this stage concerns subcontractors supplying off-the-shelf products. In practice, this exclusion seems complicated to implement because one of the two types of data mentioned above is often involved in the relationship, around the support, contractualisation or support.
This represents today a chain of nearly 300,000 companies worldwide. The introduction of the certification requirement will take place in stages, but the rise in importance will be very rapid. In 2026, it will have become a default clause for all contracts initiated by the DoD.
When a client of this size implements new constraints, the question of propagation beyond the initial circle immediately arises. Some non-defence US state actors, such as the National Education Department, have clearly indicated their interest in this certification and the possibility of including it in their own medium-term contracts.
Moreover, as the certification budgets of the various actors are limited, it is likely that the CMMC will gradually cannibalise other standards, and the number of actors impacted will de facto be much larger than the circle initially identified.
General principles
The CMMC is built around a set of processes and good practices to be implemented, organised around 17 domains (mainly from NIST 800-171) and through 5 levels of maturity. The two are inseparable: to be able to claim a level of certification, it will be necessary to validate both the process part and the implementation part of the security measures.
The processes, which are very similar in spirit to those proposed by the CMMI, aim to guarantee the proactive integration of cyber security into the certified structure’s DNA. They will enable, step by step, to move from a state where activities are carried out but not piloted and documented, to a complete, monitored and optimised industrialised approach.
The differents levels are described in the opposite figure and explain how the expectations on the process and the practices evolve.
The 5 levels of CMMC
Processus: Performed
The necessary actions are implemented, but are not documented or specifically monitored.
Measures: Basic
The measures to be implemented are basic measures, focusing on the protection of data of the type “information provided by the DoD under contract and not intended for public dissemination”.
Processus: Documented
The actions taken and the rules in force are documented, by domain.
Maesures: Intermediate
The associated measures are transitional measures allowing a structured move from level 1 to level 3. They incorporate certain rules for unclassified controlled data.
Processus: Managed
The cyber security policy is concretely managed: resources identified, action and training plan defined, etc.
Maesures: Good
The measures complement the protection required for unclassified controlled data.
Processus: Reviewed
An evaluation mechanism is in place to analyse the cyber policy and allow for its regular review.
Mesures: Proactive
The measures seek in particular to implement an effective defence against advanced threats (APT type).
Processus: Optimised
The approach is standardised and optimised for the whole structure, by domain.
Mesures: Avanced
The measures complement and deepen the protection against APTs.
EBIOS Risk Manager & CMMC
Risk analysis is an elementary component of any information systems security policy. It is also an important and transversal part of CMMC implementation. It is mainly cited in the “Risk Management” field, and its integration becomes explicit from level 2 via the “RM.2.141” practice: Risks to the organisation’s activities must be assessed regularly. The expected approach then becomes more precise, level by level. The methodology to be used is not imposed, but the parallel between EBIOS RM and the proposed measures is quite direct.
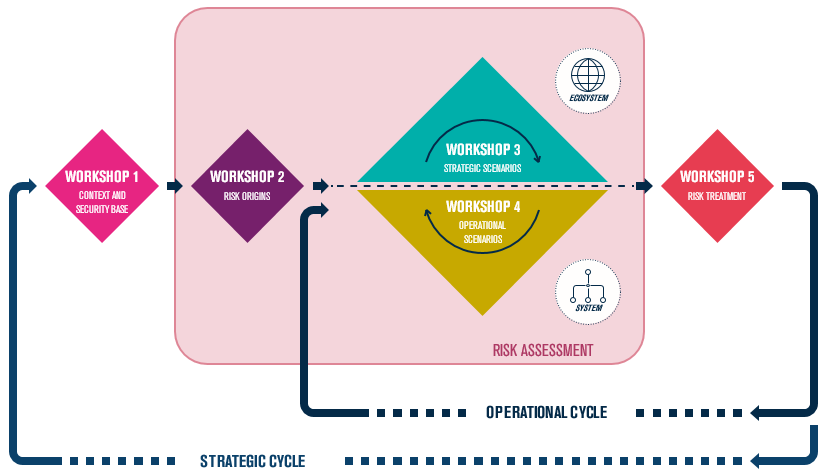
As a reminder, and without going into detail, the approach proposed by EBIOS RM is based on 5 workshops:
- Workshop 1: definition of the perimeter and what we wish to protect, identification of what is feared, definition of the security base
- Workshop 2: identification of attackers and their motivation
- Workshop 3: focus on the ecosystem and its possible exploitation
- Workshop 4: definition and evaluation of the likelihood of success in the event of an attack
- Workshop 5: Remediation
The letter and spirit of EBIOS RM emphasises agility and communication. These two principles directly echo the notion of levels exploited in CMMC. Each EBIOS RM workshop can be used and built as the CMMC approach is implemented, and serve as a guideline for its deployment.
More concretely :
- What do we want to protect?
- What is the impact on the organisation's missions?
The work of verifying compliance and the associated remediation is very naturally carried out through reflection on the security foundation. Nevertheless, it must be seen here as an extensive approach, as involuntary risk is not explicitly ruled out in CMMC.
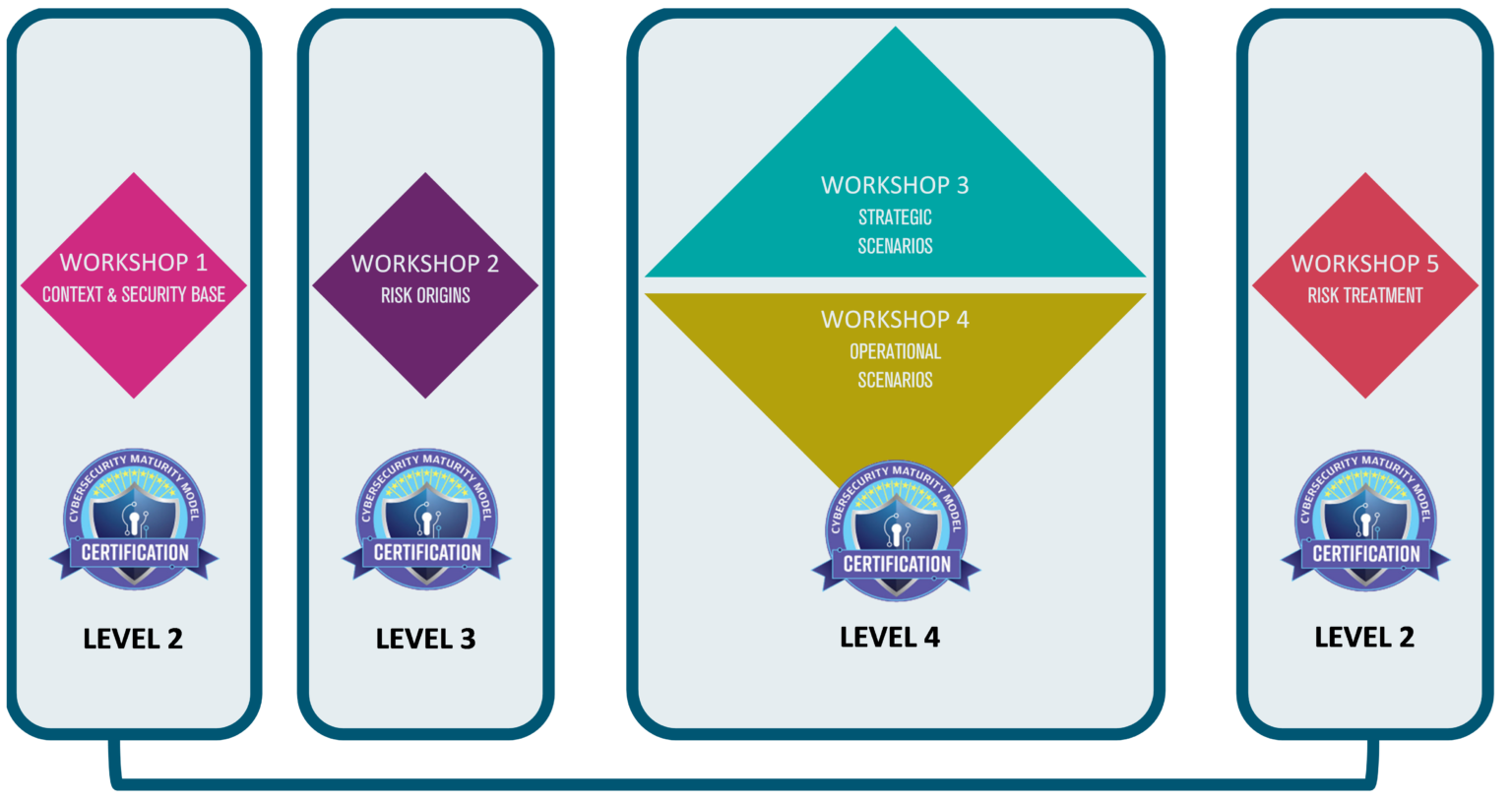
The identification of risk typologies, their sources, and the definition of evaluation rules (RM.3.144) is covered in particular by Workshop 2, and generally speaking by the risk analysis itself.
The work around the ecosystem (workshops 3 & 4) covers the need to identify and integrate subcontracting in the implementation of the maturity model (RM.4.148).
L’identification des typologies de risques, de leurs sources, et la définition des règles d’évaluation (RM.3.144) est couverte en particulier par l’atelier 2, et de manière générale par l’analyse de risques en elle-même.
Le travail autour de l’écosystème (atelier 3 & 4) recouvre le besoin d’identifier et d’intégrer la sous-traitance à la mise en œuvre du modèle de maturité (RM.4.148).