The EBIOS RM method was updated in 2018, and the ISO 27005 in November 2022. Both updates are major, and redefine the focus on risk management based on the business, cybersecurity and privacy. The objective of this article is to clarify the link and the existing relationship and compatibility between the ISO standard and the French method.
The ISO 27005 standard describes the general outlines of a cyber risk management: context establishment, identification and evaluation of the risks taken, and the risk treatment options to reach acceptable residual risk levels. It introduces a risk assessment process in accordance with the ISO 31000, without giving a method stricto senso. Strongly linked with the ISO 27001/27002 standards and using the vocabulary mainly defined in ISO 27000, the ISO 27005 uses, like many management systems, the logic of iteration and continuous improvement.
EBIOS RM is a security risk assessment method that is now 25 years old. It was defined by the ANSSI, with the support of the EBIOS Club. It describes in details the procedure to be followed to carry out a security risk assessment (general steps and good practices).
The latest update of the method is highlighting agility, and representativeness rather than exhaustiveness: the idea is no longer to identify all the security risks, but only the most important or significant ones. It is also intended to be more flexible based on the organisation’s maturity and the associated objective.
Questions about the link between the ISO 27005 & EBIOS RM are regularly raised, for the following reasons:
- In France, EBIOS RM is widely known and used as a security risk assessment method. It is the national method and is referenced by ENISA. However, it does not have the same recognition beyond our borders, where the reference is the ISO 27005 framework instead of national methods.
- As EBIOS RM is a method, by definition it is an instantiation of ISO 27005, and by consequence it isnot a standard. By comparison, the ISO 27005 is a standard providing a model, but not specifying a method to implement it. In fact, when implementing an ISMS that follows the ISO 2700x family of standards, the need immediately arises to identify whether or not the risk assessment method selected is compatible with the chosen normative framework.
Link between ISO 27005 activities & EBIOS RM workshop
What are the links between the EBIOS RM process and the ISO 27005:2022 process? Can we say that EBIOS RM is ISO 27005:2022 compatible ? This article, over the next few paragraphs, details this compatibility and the link between each activity and workshop.
General workflow
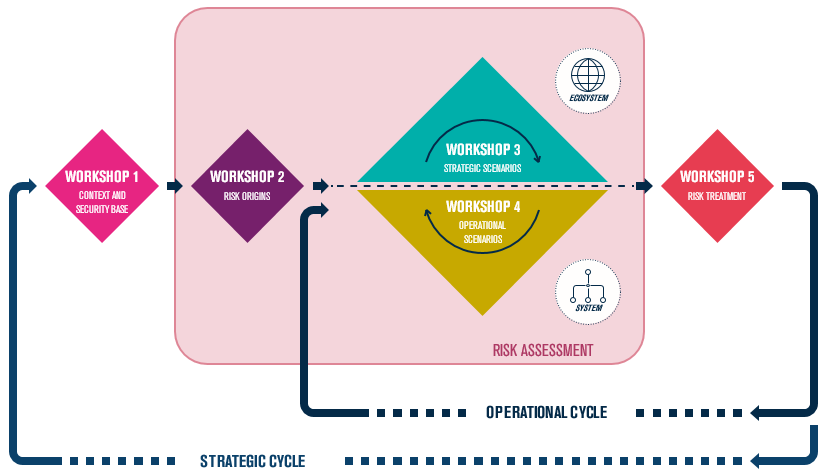
EBIOS Risk Manager
EBIOS proposes an approach built around 5 workshops. Each workshop importance will change according to the objective set for the risk assessment and the maturity of the scope concerned. The proposed workshops are as follow:
- Defender point of view: what needs to be protected, and why ? Workshop 1 focus on the scope of the study. The analyst seeks to define precisely the boundaries (where the study begins and ends), the situation with regard to the legal, normative or regulatory status (the security base), and what the business team fears.
- Who is the attacker and why is he attacking ? Workshop 2 is focusing on the attacker, whom we will try to evaluate in terms of resources and motivation.
- Where will the attacker start ? Workshop 3 focuses on the ecosystem (everything that interacts with the perimeter without being part of it) and its possible use by an attacker.
- How will the attack be performed ? Workshop 4 tries to evaluates the likelihood of the possible attack paths identified, by looking at the operating methods (described in operational scenarios) used by an attacker.
- Which security treatment options for the risks identified ? Workshop 5 is a classic remediation activity: now that the risks have been identified, how can they be reduced ? Is the activity too risky to pe performed ? Should they be dealt with, transferred, can they be accepted ?
ISO 27005
The approach proposed by ISO 27005 also includes 5 major steps:
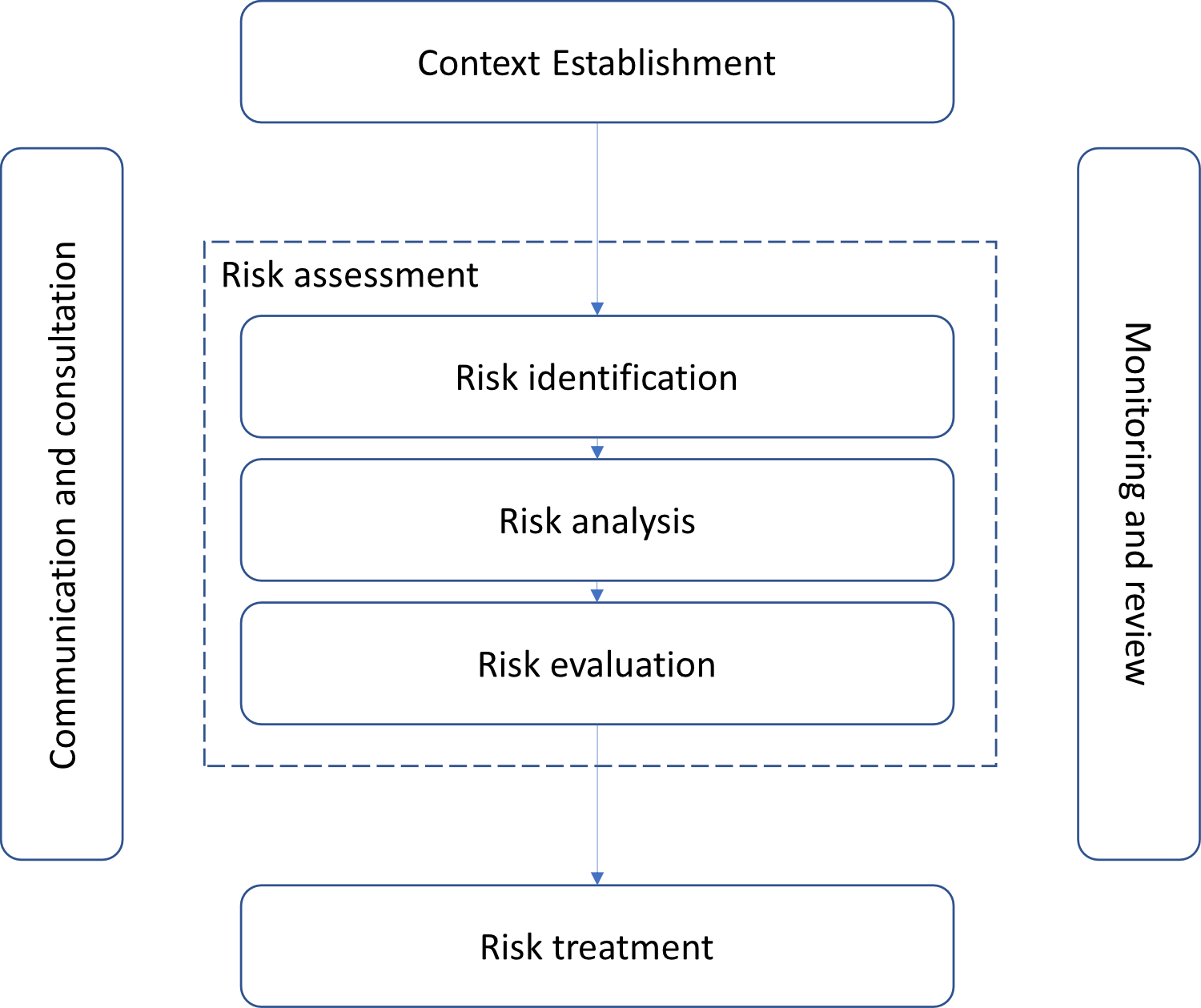
The ISO 27005 is also adding two other parallel activities: communication and the monitoring & review activity.
The context establishment
ISO 27005 starts with the identification of the requirements of the stakeholders, including standards, contractual requirements ,regulations, possible addition from the SSIP, etc. It is a straight forward link to the EBIOS RM activity of establishing the security baseline.
Non-compliances: In both cases, the main idea is that identified non compliances will provide a clear view of the maturity of the studied perimeter, and feed the following subsequent risk assessment workshops. Indeed, each non-compliances or exceptions will be considered to assess the likelihood of the risk scenario to which the system under study is exposed.
Scales: To answer to how the risk assessment can be done and risk levels evaluated scales & matrices are identified: the severity of the feared events, the likelihood, and the policy of acceptance for the identified risks.
Consequences: For the evaluation of the severity, an important change of word appears: the ISO 27005 does not speak of feared events, but uses the term consequence (previously called impact). The evaluation is done through the criteria of consequences, and their severity, through the identification of the damage done. It simply corresponds to the notion of impacts existing in EBIOS RM.
Likelihood: For the likelihood, the ISO 27005 proposes the use of scales based on probability of occurrence or frequency. EBIOS RM let the user free to define its evaluation mechanism for likelihood, and is more focused on the success realism. The likelihood paramaters from an EBIOS RM risk assessment (if the method guides are followed) will probably require post-processing or adaptation in this case, following the ISO recommendations.
EBIOS RM has, in theory, a more continuous approach to the construction of these elements (they are defined as the study progresses), but in practice this is often a subject to define from the beginning. Criteria should be aligned with the one already existing in the company or organisation, to ease sharing the results obtained afterwards.
The last criterion is for the risk acceptance: according to the previous criteria (severity and likelihood to define a risk level), how does the organisation behave facing risks identified? It is directly linked to the security risk treatment. This assessment of risk appetite is not specific to the cyber sphere. The ISO 27005 and EBIOS RM are this time completely aligned.
Risk assessment
Risk assessment, in the ISO 27005, involves three steps: identification, analysis and evaluation.
Risk identification
Risk identification according to ISO 27005 is the process dedicated to recognising and describing risks. It involves determining the sources and what can happen. The objective is to have at the end of this activity a list of risks that can lead to the realisation of consequences, threatening the achievement of the identified security objectives.
In EBIOS RM, the risks identification is not monolithic. It is carried out step by step, and each workshop will help to construct and specify it:
- The first EBIOS RM workshop identifies the feared events and what needs to be protected (primary/business assets)
- The second EBIOS RM workshop filters risk sources and target objectives associated to retain only the most relevant ones. It should be noted that there is a major difference in semantics between EBIOS RM and ISO 27005: EBIOS RM is only looking for intentional sources (the security baseline manages the accidental one), while ISO 27005 explicitly includes unintentional sources. Furthermore, ISO 27005 makes a distinction between the short-term objectives of the attacker and his long-term objectives (desired end state), whereas EBIOS RM does not explicitely distinguish the two elements. This topic is described in the (informative) annexes
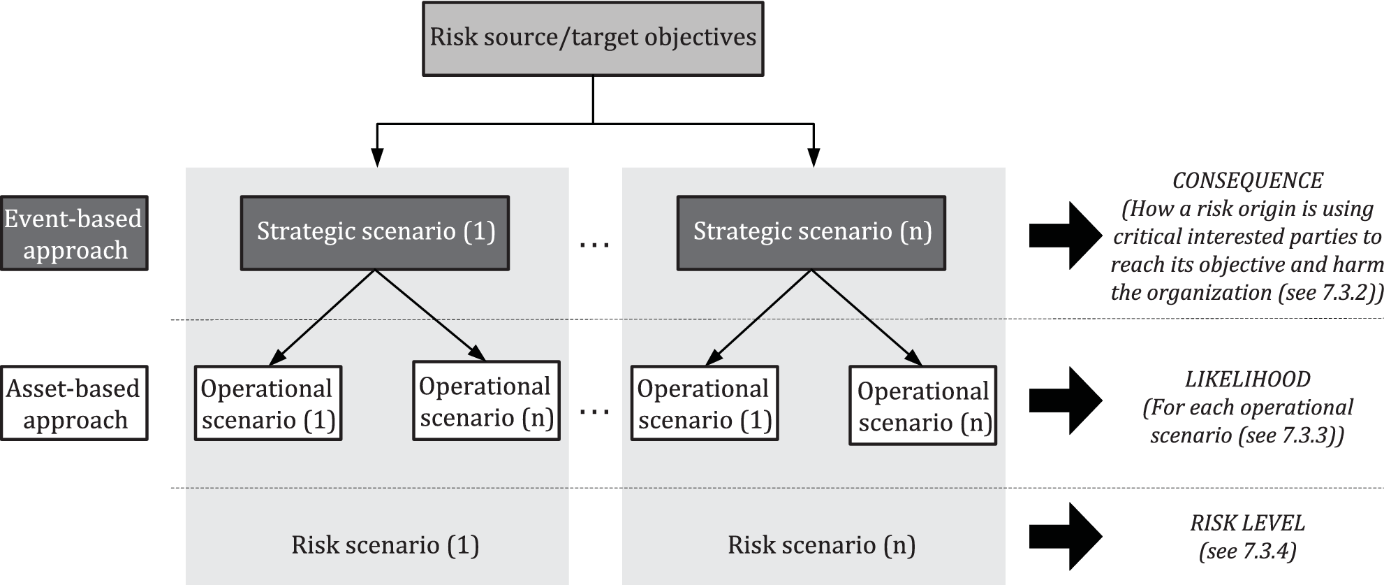
- The third EBIOS RM workshop creates the link between feared events, risk sources and primary assets: the combination of these elements allows to identify risk scenarios, and thus to reach the objective of risk identification set by ISO 27005
ISO 27005 identifies two approaches for risk identification: event and ecosystem-based or supporting assets based. Annex A clearly shows the direct link between these two approaches and workshops 3 (respectively 4) of the EBIOS RM method.
Vulnerabilities: There is, however, a concept spelled out in ISO 27005 that is not directly identified in EBIOS RM: the vulnerability management. In conjunction with the workshop 4 (or the asset-based approach), the integration of vulnerabilities into the risk assessment process allows the organisation to propose a specific treatment of the risk at a detailed level. This proposal can be seen as an extension to the EBIOS RM approach, but is in no way contradictory.
Risk analysis and assessment
This step is designed to evaluate the identified risks through a set of criteria determined beforehand. This work will enable each risk to be associated to a risk level defined as a combination of consequence severity & likelihood defined during the assessment. It is (again) carried out during the various EBIOS RM workshops:
- The willingness to act in workshop 2, known as "relevance";
- Severity is assessed during Workshop 1, when the feared events are identified
- Likelihood is assessed in a general way in workshop 3, or/and in a detailed way in workshop 4. In both cases, and whether in EBIOS RM or ISO 27005, the difficulty of the exercise and its necessary subjectivity are underlined
These values will then be used to classify the risks by comparing tem with the risk acceptance criteria defined by the organisation: this equivalent to placing each risks on a risk acceptance matrix, where each cell reflects these criteria.
Risk treatment
The ISO 27005 proposes a general treatment of risks split in several steps:
- Choosing the most appropriate risk treatment option, assuming that reduction is the priority choice
- Preparing a Statement of acceptability (SoA), in line with Annex A of ISO 27001
- Formalising a risk treatment plan
- Accepting the residual risks
EBIOS RM simplifies the choice of the risk treatment option, giving priority to reduction or acceptance according to risk levels. The notion of a SoA does not appear either, but it is a documentary production that can be made from the results obtained in each workshop. The risk treatment plan definition and the acceptance of residual risks are nearly done in the same way.
Transversal process: communication and monitoring
The ISO 27005 presents the communication process in the following way: “information on risks, their causes, consequences, likelihood and the means of control implemented to deal with them are communicated […] to the interested parties”.
This communication is present in EBIOS RM, but is not identified as a specific activity. Instead, it is an integral part of each step, because it is part of the mindset of the method: risk assessment is by definition a tool for sharing and communication. The several graphic representations (radar, strategic and operational scenarios, etc.), but also the strong desire (in terms of vocabulary and implementation) to place the business as the central point are the concrete proofs.
Monitoring scenarios: Among the communication and monitoring activities, the translation of risk scenarios into monitoring scenarios and correlation rules to be integrated in the detection tools of an organisation ensures that the most critical risks can be detected. Or at least it can help an organisation to identify a lack of detection capability. This part, which makes the link with ISO 27035 (standard on security incident management) and SOC activities, is not in the EBIOS RM method but comes from a contribution of the Club EBIOS (French security risk assessment expert community) resulting from the feedback of its practitioners.
Trigger: For the review and monitoring process, the ISO 27005 provides details on the implementation of the monitoring of identified risks. The notions of strategic and operational cycles are taken up stricto senso, but the ISO 27005 introduces the trigger notion, a condition that effectively initiates the risk assessment update.
Summary of wording equivalences
| EBIOS RM | ISO 27005:2022 |
|---|---|
| Stakeholder | Context establishment |
| Strategic scenario | Event based approach / Strategic scenario |
| Operational scenario | Asset based approach / Operational scenario |
| Feared event | Consequence |
| Intermediate event | Intermediate consequence |
| Business asset | Primary asset / business asset |
| Supporting asset | Supporting asset |
| Risk origin | Risk source |
| Threat level | Danger level |
| Security continuous improvement plan | Risk treatment plan |
| Impact | Consequences criteria |
| Security need | Security target |
| Severity | Severity |
| N/A | Trigger criteria |
Conclusion
The general approach proposed by ISO 27005 allows to identify the necessary steps to perform a risk assessment, without making mandatory a specific process to perform it. The main novelty of ISO 27005 is the dual approach by events and/or by supporting assets, and this dual approach is a core part of EBIOS RM. The concepts used on both sides are then coherent, even if few are only explained/detailed on one side or the other.
Authors

Product Owner Cyber – ALL4TEC

Risk Analysis and Cyber Team Leader