The PIA and EBIOS Risk Manager guides are very similar in theme, vocabulary and method. Operationally, the two professions driving these analyses, respectively the DPO and the CISO, are very often carried or assumed by the same person or the same team.
The need to homogenize the analyses carried out and to reuse both knowledge bases and methodologies as much as possible is important. To make this possible, we propose to equip both the realization of your PIA and your EBIOS Risk Manager analyses with our Agile Risk Manager software.
Why Using EBIOS RM to make a PIA ?
The GDPR came into force nearly two years ago now, and the CNIL has made a considerable educational effort to support companies and institutions in its implementation. In the heart of the GDPR, when a processing of personal data is likely to generate a high risk for the rights and freedoms of individuals, the PIA is a real cornerstone. It must allow for a detailed analysis of the risks involved, their likelihood, and the associated seriousness.
At the same time, ANSSI has updated its EBIOS reference method to propose a new iteration, more agile, concentrated, and more easily scalable: EBIOS Risk Manager. This method has been created to be used by any type of organization, and allow them to clearly identify the digital risks to which they are exposed.
When analyzing the documentation proposed by these two organizations, we immediately see that if the two topics are not identical, their two spaces are intertwined. There is a proximity of theme, vocabulary, methodology, which is significant. Operationally, the two professions piloting these analyses (the DPO for the PIA, the CISO for the EBIOS RM analysis), are very often carried out or at least assumed by the same person or within the same team.
Once this proximity has been identified, the need to homogenize the analyses carried out, and to reuse both knowledge bases and methodologies as much as possible, becomes apparent. Concretely, the question is : can we use the EBIOS Risk Manager method to perform a PIA ?
A PIA From a legal perspective
There is no difficulty from a legal point of view. While the application of the GDPR requires (according to specific rules) the completion of an PIA, it does not specify a specific method for doing so. Details are available on the EU website (article 35.7). One can read that it is obligatory to find there :
- A systematic description of the processing operations envisaged and the purposes of the processing, including where appropriate the legitimate interest pursued by the controller;
- An assessment of the necessity and proportionality of the processing operations in relation to the purposes;
- An assessment of the risks to the rights and freedoms of data subjects in accordance with paragraph 1;
- The measures envisaged to address the risks, including safeguards and security mechanisms to ensure the protection of personal data and to demonstrate compliance with this Regulation, taking into account the rights and legitimate interests of the data subjects and other persons affected.
From a methodologic perspective
The parallel with between the two methods is quite direct, even if we must remain attentive to the difference in semantics between the vocabularies used. The same word does not always have exactly the same meaning in both contexts.
Description of a PIA by the CNIL
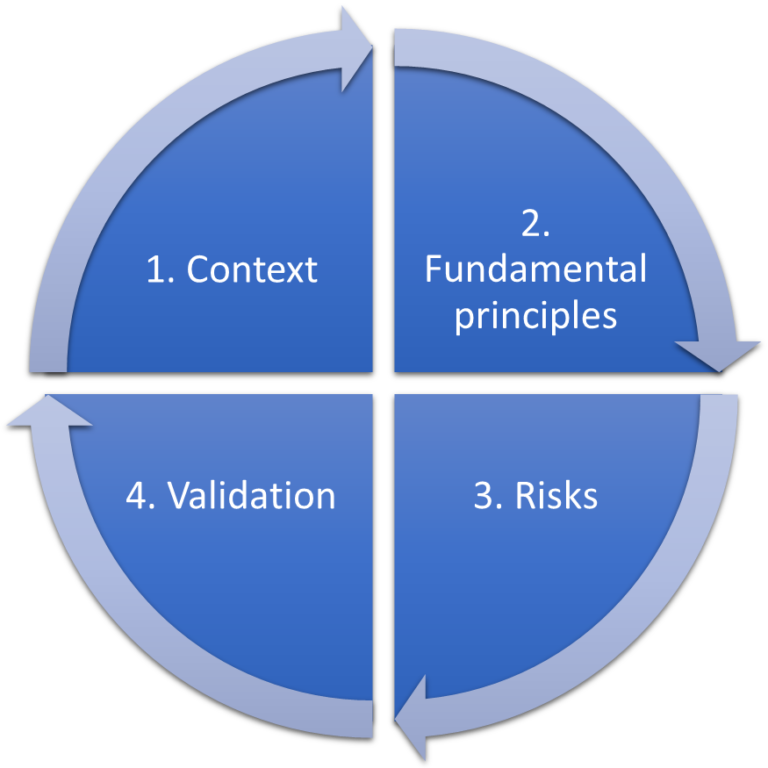
The conduct of an AIP consists of 4 major steps:
- Delineate and describe the context of the treatment(s) under consideration;
- Analyse the measures ensuring compliance with the fundamental principles: proportionality and necessity of the processing, and protection of the rights of the data subjects;
- Assess the privacy risks related to data security and verify that they are adequately addressed;
- Formalize the validation of the PIA in the light of the above elements or decide to revise the previous steps.
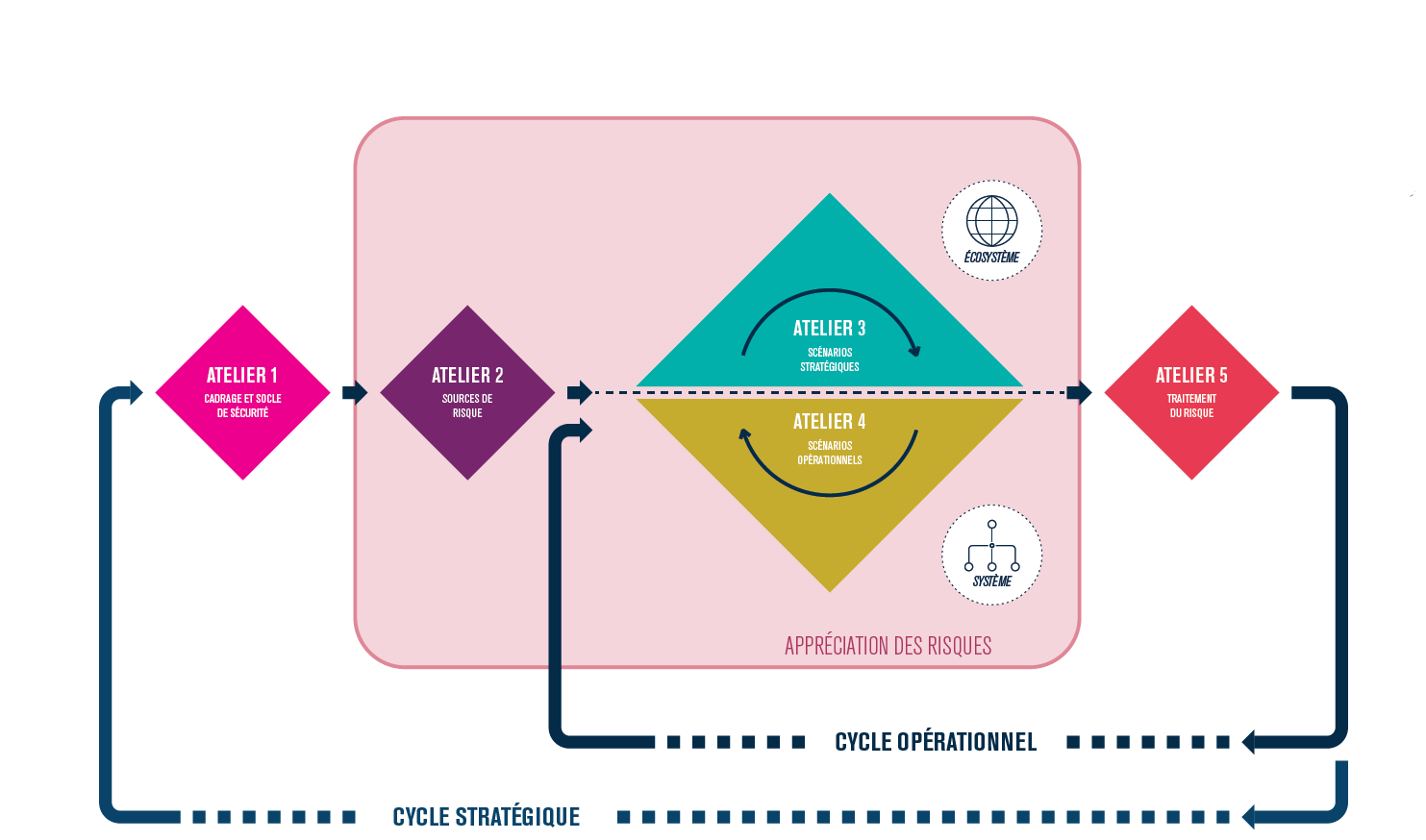
Description of EBIOS Risk Manager by the ANSSI
The method is built around 5 workshops :
- Context and security base
- Risk origin
- Strategic scenarios
- Operationnal scenarios
- Risk treatment
How to Realize your PIA with EBIOS RM
Step 1 : Define the context (EBIOS RM : workshop 1)
The context definition step (PIA Step 1) can be carried out very directly in Workshop 1 Ebios RM. Personal data, the heart of the AIP, are treated as business values.
It should be noted that the scope of the PIA is broader than that initially proposed by Ebios RM, as it includes for example physical elements (paper media, etc.). Data carriers (PIA) can be directly treated as support assets (EBIOS RM).
Step 2 : Asses existing measures (EBIOS RM : workshop 1 and 2)
The second stage of the PIA (fundamental principles) aims to assess the measures already in place and the need for the treatment carried out.
This stage is covered in an EBIOS RM cycle by the definition of the safety base (workshop 1), even if there is necessarily some gymnastics to match the voluntarily generic notions of EBIOS RM and the more specific ones of the PIA.
Step 3 : Study the risk (EBIOS RM : workshop 3 and 4)
The third stage of the PIA covers the study of data security risks. It is a subset on which the approach proposed by EBIOS RM becomes particularly value-creating.
The business values/supporting assets have already been identified during the first step.
The sources of risks are a notion explicitly present in both methodologies, even if, once again, the scope of PIA is much broader: it includes both intentional and unintentional sources of risk and stakeholders in the sense of EBIOS RM.
This difference in vocabulary will require a specific approach: some sources of risk do not have an intended purpose. To compensate for this absence, neutral objectives will be defined, i.e. objectives without any particular semantics.
Workshops 3 & 4 (strategic and operational scenarios) can then be completed in the classic way. The treatment of the threat assessment associated with the stakeholders is here optional and to be carried out on a case-by-case basis.
Step 4 : Validate the measures (EBIOS RM : Workshop 5)
The final stage of the PIA is a general remediation and validation stage. The first sub-step is the identification of the security measures necessary to ensure compliance with the fundamental principles and data security.
This is an activity covered by Workshop 5 in EBIOS RM, as is the identification of residual risks and the creation of the action plan. The second part of this step in the PIA corresponds to a formal validation, via a specific form. It is a purely documentary activity, compatible with the EBIOS RM approach.