The EBIOS Risk Manager method continues its deployment and its adoption is accelerating. Nevertheless, a large capital of EBIOS 2010 analyses is still in place and valid. Can they be migrated to EBIOS RM and for what gains?
A bit of history
- The first official version (1995)
- An update (2004)
- A significantly development, in 2010 (EBIOS 2010 )
- An other sifnigicantly development in 2018 (EBIOS RM)
Should I switch to EBIOS Risk Manager ?
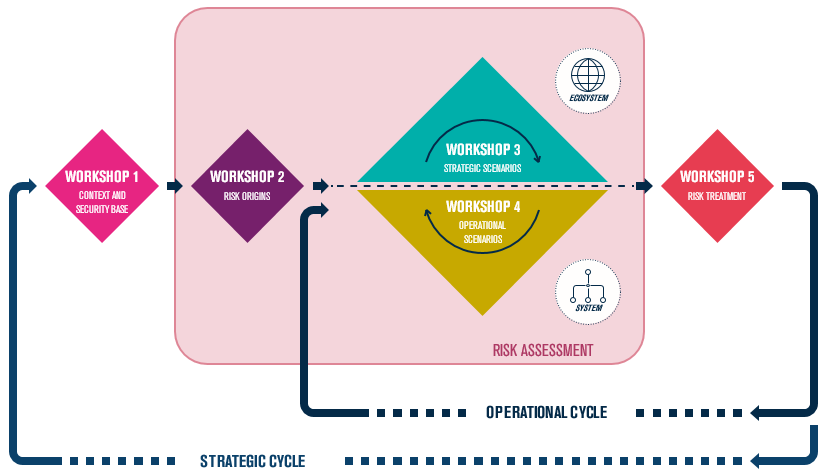
EBIOS 2010 talks about Modules, EBIOS RM talks about Workshops. This change of vocabulary is not insignificant, and really supports the will of communication and exchange carried by this new iteration of the method.
The idea of the Workshop implies working with several people, in a direct way, and to integrate as much as possible actors who remained in the past on the fringe of the analysis. Each workshop will require the identification and prioritisation of elements, and this requires an accurate vision through the trades, and the ability to make decisions through those in charge.
In addition, and contrary to what EBIOS 2010 proposed, each workshop will be able to produce elements directly exploitable to improve the global cyber posture.
At the end of workshop 1, we will be able for example to consider the perimeter of the security base not applied, at the end of workshop 3 to identify the measures associated with the ecosystem, etc.
The transition from EBIOS 2010 to EBIOS RM therefore requires above all a change of posture: agility and continuous improvement become central in this new approach.
A DIFFERENT CONSTRUCTION AND APPROACH
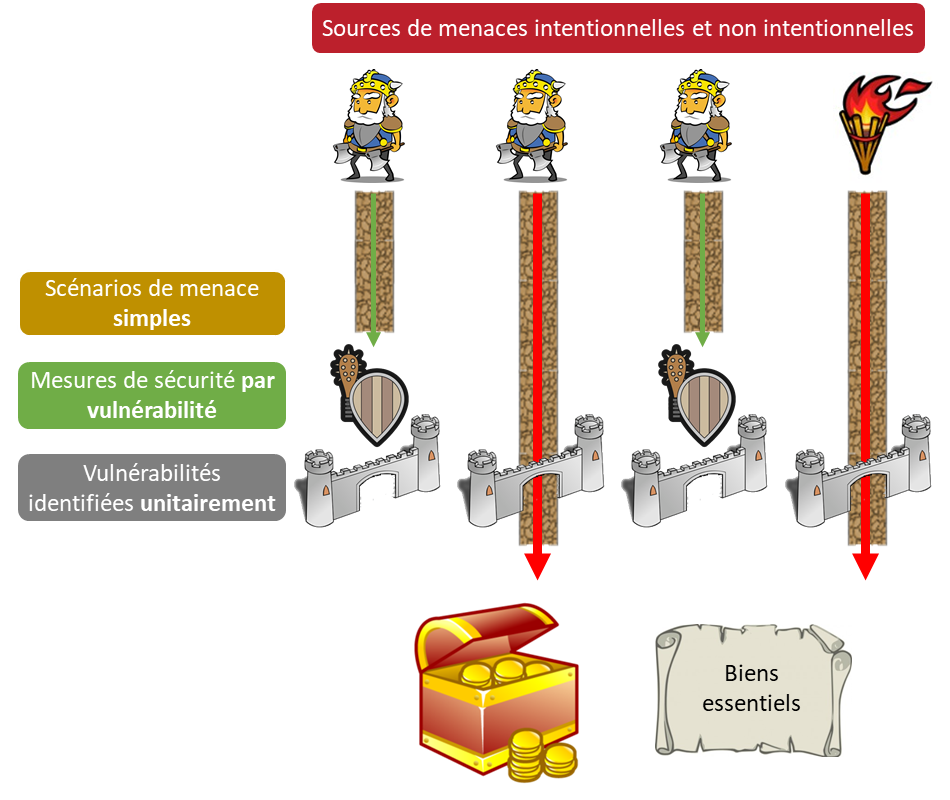
EBIOS 2010 required a very broad approach to identifying vulnerabilities and supports, with the corollary risk of integrating many peripheral elements into the perimeter, and the need for real exhaustiveness.
This meticulous and often consequent work easily allowed industrialisation. This inventory was partially abandoned by EBIOS RM.
The construction of the context is done from the missions (and not towards the mission), and the identification of the vulnerabilities now pursues another goal: to allow the definition of the possible elementary actions and to ensure the relevance of the operational scenarios of workshop 4.
Re-usable elements
Directly, a large part of the data from the existing EBIOS 2010 analyses can be directly reused in EBIOS RM: supporting assets (be careful with the scope, however), business assets (in the form of business values).
The security repository will be able to feed the security base quite simply. The scales are also globally reusable (severity, likelihood, etc.) as well as the impact knowledge base.
Then there are the elements for which correlation is possible but less direct:
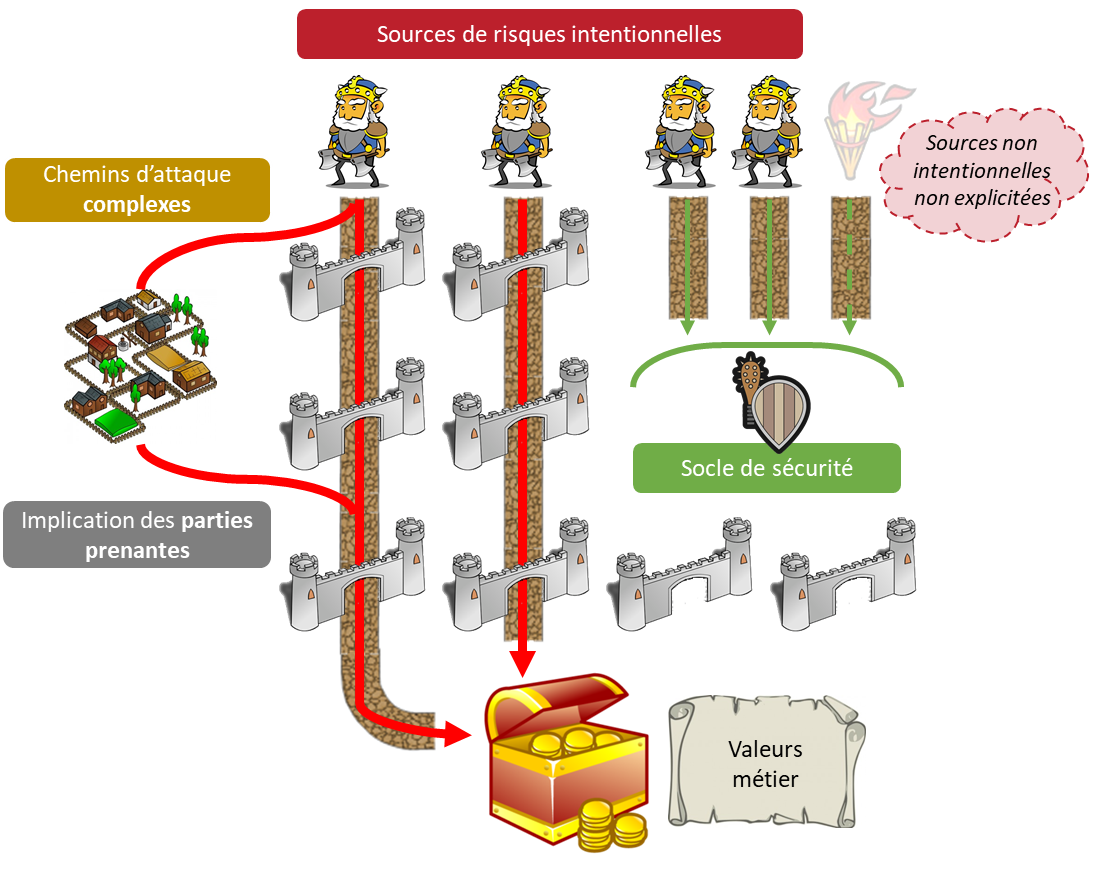
The EBIOS 2010 threat sources (Module 1) are partially covered by the EBIOS RM risk sources. Indeed, all the unintentional part is no longer explicit, as it is normally absorbed by the security base (Workshop 1). At the margin, some sources of threats can also be reused for the definition of the ecosystem stakeholders.
The feared events defined in EBIOS 2010 are built quite mechanically based on criteria and security needs. If these notions have not disappeared in EBIOS RM, they are nevertheless less explicit. The objective is to make the feared events less generic and more specific to the job/perimeter covered by the analysis. It will therefore be necessary to pay attention to their reformulation.
Threats in the sense of EBIOS 2010 are global actions, of very high level, that can be associated with a source in order to build high level threat scenarios. This type of approach no longer has a direct equivalent in EBIOS RM. Nevertheless, depending on the level of detail of the existing analyses, part of the data can be used to feed the basis of intermediate events (Workshop 3), within the strategic scenarios within the framework of an EBIOS RM analysis..
Significant differences
The differences between the two approaches are significant enough to call for caution when taking up the other elements. The risks identified will be very different in nature: EBIOS 2010 identifies simple, precise risks, whereas EBIOS RM focuses on much richer and more complex scenarios and risks.
It is therefore important not to seek to identify the same thing, or the same volume of risks, but to change one’s approach by aiming to build an iterative risk reduction strategy.
A mandatory challenge for tangible gains
Les différences et les points communs abordés dans cet article permettent de construire une première approche structurée d’une migration : récupération et élagage des données, re-découpage de certaines bases, puis un nouveau cycle de définition des risques et leur évaluation.
Cette approche doit être adaptée (une analyse EBIOS 2010 d’un système informatique en univers hospitalier n’offre pas le même contexte que celle d’un système de défense militaire), et il ne faut pas faire l’économie d’une remise en cause significative des résultats des analyses précédentes : le gain et la pertinence de la migration seront au rendez-vous.